Hi, I’m Arpan Padmani
Full Stack Developer
Full Stack Web App Developer with 4+ years of hands-on experience in building high-performance, scalable web and mobile apps.
Application Development
I am Providing Android & IOS Mobile Application Solutions with Great UX.
VIEW DETAILS VIEW DETAILSDevOps & Deployment
I Providing Cost Effective and Robust Cloud Solutions which increase your Business.
VIEW DETAILS VIEW DETAILSDiscover My Recent Projects
Testimonials
"Arpan delivered a stunning website that not only looks beautiful but also performs flawlessly. From design to deployment, everything was seamless. Highly recommended!"
Krupesh Khurana
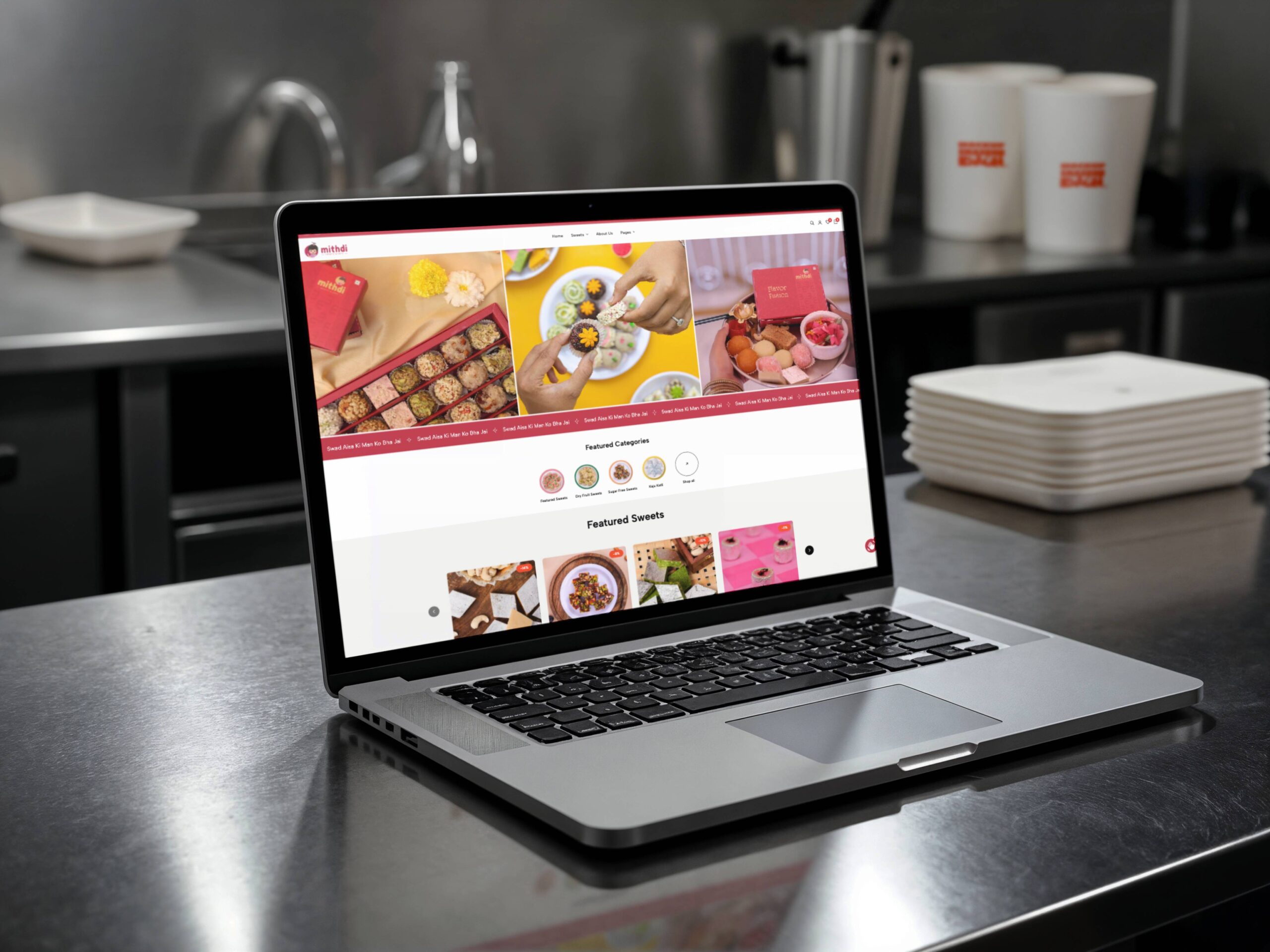
Creative Apes Design"Our new e-commerce site was up and running within days — fast, mobile-friendly, and optimized for SEO. These guys know what they're doing!"
Krrish Chovatiya
Mithdi SweetsFrom wireframes to my Web store deployment, the team handled everything. We appreciated the regular updates and proactive suggestions.